Now that you can have a full GnuPG on your Android device with Gnu Privacy Guard for Android, the next step is getting keys you need onto your device and included in Gnu Privacy Guard. We have tried to make it as easy as possible without compromising privacy, and have implemented a few approaches, while working on others. There are a few ways to get this done right now.
Gnu Privacy Guard registered itself with Android as a handler of all the standard OpenPGP MIME types (application/pgp-keys, application/pgp-encrypted, application/pgp-signature), as well as all of the OpenPGP and GnuPG file extensions (.pkr .skr .key .sig .asc .gpg .bin). This means that users just have to share a file to Gnu Privacy Guard using any of the standard Android methods, these files can be launched from an email attachment, opened from the SD card using a file browser, clicked in the Downloads view, etc.
So if you want to quickly send your whole public keyring from your laptop to your mobile device, you can just grab the database file directly from GnuPG and copy it to your SD card. Here is how:
- plug your device into your laptop via USB so you can copy files to the SD card
- find your GnuPG home folder (on GNU/Linux and Mac OS X, it will be in
~/.gnupg/pubring.gpg, on Windows it is%APPDATA%\gnupg) - In your GnuPG home folder, copy pubring.gpg to your device’s SD card
- unmount and unplug your device
- on your device, open your favorite file manager app (OI File Manager, Astro, etc)
- go to the SD card
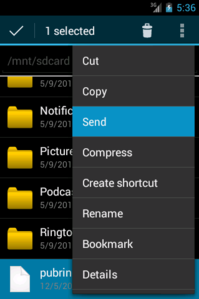
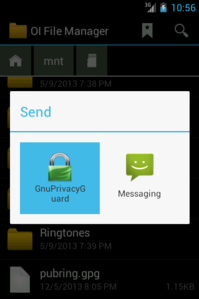
- long-click on pubring.gpg and share it to Gnu Privacy Guard
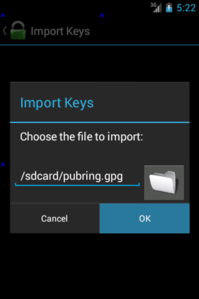
- click OK on the Import Keys dialog
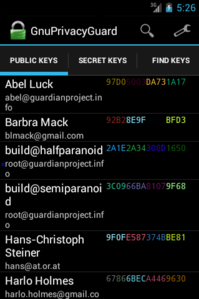
After that, Gnu Privacy Guard will do the rest. Give is some time to sync to the Contacts database, then you’ll see all of your keys from your desktop are now in your People app and are listed in Gnu Privacy Guard itself. You can now encrypt files to any of those keys, or verify files signed by any of those keys. Here are a couple screenshots to illustrate key points in the process, using OI File Manager:
There are many ways to get the keyring files like pubring.gpg to your device: you can also share the keyring files via email, chat, or even services like Dropbox or Google Drive. Then once the files are on your device, you can import them using the same procedure as above. But keep in mind that you are sending your whole collection of secure contacts to that service, which will have full access to read it. If you have any worries about leaking your keyring to anyone, then a good method is to copy it directly to the SD card.
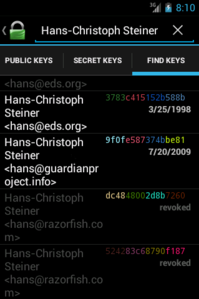
You can also search and download keys via the public pool of OpenPGP keyservers. If you already know someone’s keyid or fingerprint, you can search using that. Otherwise, you can search based on name or email address. But be careful! Downloading a key from a keyserver does not give you a key you can trust. Anyone can upload a key to the keyservers, and they can make that key have any name or email address. Downloading from the keyservers is a convenient way to download a key, but you must verify the key’s fingerprint with the person you are trying to find.
In conjunction with theMonkeysphere project, we developed a standard URI scheme for sending OpenPGP key fingerprints. For example, you can find my key ID here: openpgp4fpr:9F0FE587374BBE81. This provides a clickable way to get an OpenPGP key. On an Android device with Gnu Privacy Guard installed, you can click on this link to download my key from the keyservers. This URI scheme also works well in QR Codes. Scan this QR Code on your device with an app like Barcode Scanner, and click Open Browser, and Gnu Privacy Guard will download my key to your device.
There are other ideas out there that we also want to support. For example, OpenPGP Keychain includes a way to transmit the whole public key via NFC. This allows people can swap keys directly from phone to phone without having internet access at all. But NFC is quite slow to transmit data so the devices need to be held together for a while until the whole key is received. NFC could be used to rapidly transmit an openpgp4fpr: URI, and then the whole public key would be fetched from a keyserver, but that then requires internet access and also leaks a bit of metadata to the internet. A better technique would be to transmit the entire public key over Bluetooth, using NFC to setup the Bluetooth session. We’re also looking at ways to do this via WiFi and Bonjour (mDNS) local service advertisements.