If you see me dancing or signing with my phone in my hand, I may not just be having a great time, but also creating an encryption key. Part of the issue with security is that it can often be difficult to implement or an added step in what users want to be an easy and seamless process. What if we can make secure and private communications fun and easy?
This past weekend, a bunch of members of the Guardian Project team found ourselves at the Wall Street Journal Data Transparency Hackathon. The Journal put this together in order to “invite developers to help build free Web tools that promote data transparency and control.” The tracks were divided into:
- Scanning: Enhancing technology that scans the Web to reveal tracking
- Education: Helping people see how much information they share
- Control: Improving software that helps people control sensitive information
Tracks were led by Ashkan Soltani, an independent researcher and technical adviser to the Journal; Brian Kennish, a Web developer and founder of Disconnect; and Jacob Appelbaum, a security researcher at the Tor Project. Our teams went down the path of control, with the goal of making tools that are secure by default.
We danced our way into winning in the control category by helping the victorious Cryptocat team that has a tool for encrypted chat service right from the browser. This fantastic project blew through a number of innovations, porting into a Firefox web app, doing desktop notifications, and improved cryptographic primitives from within the browser. We helped by creating an Android app for the tool that converts dance moves into a random number generator for creating the encryption key. Just start the program, enter the name of the chat, enter your nickname, then DANCE. Starting a secure chat from a phone is now as easy as that. You can try it in your browser via their site https://crypto.cat/ or download our new Android app (either with or without Tor compatibility). And congrats to Nadim Kobeissi for this well deserved win and the team Tobias Pulls, Jacob Appelbaum, David Huerta, Joseph Bonneau and Nathan Freitas.
We sang our way into winning in a new category that the judges came up with, “soup cans and string” for Ostel, our encrypted VOIP solution. Launching an alpha version of our tool in front of some of the worlds leading experts in the security field was a risky move, but thankfully we managed to work out a number of bugs and generally received great feedback and support from the community. Over the weekend, we made progress in our alpha demo, identified additional clients that can receive calls on Mac, PC, Linux, iPhone, & Blackberry and created a new user signup system that allows users to register and immediately be sent an email with a link to their credentials via SSL. To extend the project even further, we have started compiling information on VOIP laws in countries from every continent so that the tool can explicitly be supported on as many platforms, in as many countries and in as many languages as possible. In addition to singing praise, singing (and other voice signatures) might be used in the future for entropy as the random number generator for the encryption key exchange. PrivateGSM is already doing this and it would be great to incorporate this feature into Ostel & CSipSimple later on. Thanks to Lee Azzarello, Luke Stark, Sean McIntyre and Zach Schwartz for being great members of the Ostel team.
Dancing for encryption in Cryptocat, singing for encryption in Ostel. Let us know if you have other ideas for fun ways to generate keys. We’re always looking for inspiring ideas from the community.
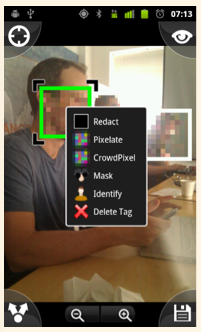
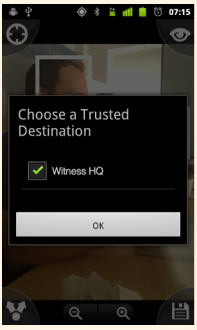
We’re even well on our way to seeing the world through encryption tinted glasses. Progress was made on making innovations in our Informacam project. The goal is to be able to snap a picture, but protect the privacy of the people in the frame by blurring their faces and the metadata connected to the event. Whie this can be crucial in a sensitive scenario, it can also be important that a judge or trusted organization can “unblur” the image and so we’re working on a way to encrypt and send those pixels. Bugs were removed, code was written, and soon enough, hopefully we’ll be able to incorporate it into the new Google Augmented reality goggles.
|
|
| Using the InformaCam “Identify” filter. | Select a Trusted Destination for your encrypted media. |
Being head down, singing and dancing encryption with our security glasses on while coding, it was easy to miss the other amazing projects in the room. I highly recommend checking out the other winners as well. They’re doing fantastic and necessary work:
- “Scanning” Track Winner: TOSBack2 – a living archive of all privacy policies
- “Education” Track Winner: PrivacyBucket – a Chrome extension that measures the extent to which individual third-party trackers can discover demographic information about the use
- Judges’ Choice Winner: Site Scoper
- “Ready for Primetime” Winner: MobileScope
- “Zuckerberg/Systrom Memorial Award for Opportunistic Optimism” Winner: Pestagram
- “Best Listener” Winner: The Price of Free
Thanks to Julia Angwin and the WSJ team for making this great event and the fantastic What They Know blog possible, to Gunner for being such an inspiring facilitator, to judges Alessandro Acquisti, Sid Stamm, Dan Kaminsky, Andrew McLaughlin and to everyone else who made this possible.


