Beyond just thinking about encryption of data over the wire, or at rest on your mobile device, we also consider physical access to your mobile device, as one of the possible things we need to defend against. Some of our apps, such as Courier, our secure news reader, include a Panic feature, enabling a user to quickly delete data or remove the app, if they fear their device will be taken from them, whether by a friend, family member, criminal or an authority figure. Most recently, with our work on CameraV, our secure evidence camera app, we have implemented a few more features that help hide the app and its data, in order to block an unintended person from seeing the photos and videos captured by it.
First, it should be said that the app utilizes IOCipher, CacheWord and the CameraCipher Library to store all media files it captures in an encrypted format, managed with a well-implemented service that handles key generation and life-cycle properly. This means that no photos and videos show in the device’s built-in gallery or photos app, and no pixels are ever written in plain-text to any storage space, internal or external. This helps a great deal in hiding that they exist, since often physical inspection of a device often starts with looking through any of the default apps, like messaging, gallery, contacts apps, and so on. ChatSecure also does this, be keeping your contacts, messages and media out of the shared, unencrypted default location.
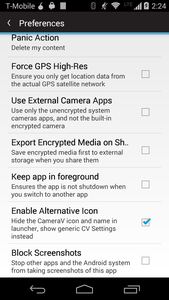
As of this week, we have had three new features to CameraV that all fall under what could be called “Stealth Mode” (though this has also been called “Boss Mode” since the days of MS-DOS when games included a quick button to change to something that looked like a spreadsheet for when your boss walked by). We took our inspiration from a few other apps, like Amnesty International’s Panic Button which hides itself as a calculator, ChainFire’s SuperSU, which allows users to switch the app icon between a few options, Courier, which blocks users and other apps from taking screenshots of the news it is display, and Orbot, which actively removes itself from the “Recent Apps” listing provided by Android. All of these features combined dramatically reduce the visual footprint that an app leaves on the device, reducing the chance that someone will discover it, even if they are looking for it.
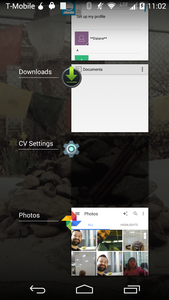
CameraV (you can get beta access here and find the source here), incorporates all of these as options for the user to activate. You can switch the default icon and app name to a more generic settings icon and “CV Settings” app name. We plan to enhance that feature to allow the user to define the icon and name, making the app able to act like a chameleon and blend in more completely. The app can be set to now allow screenshots to be taken of it, which also causes a black screen to show up in the recent apps list, stopping a casual inspection from identifying it as a photos-type app. It can also be set to not show up in the recent apps list at all, which is a more complete solution to that problem. The last piece, again taken from the aforementioned PanicButton app, is to, when the stealth icon is activated, to change the default home screen of the app to something innocuous like a calculator, so that even when the app is opened, it does not reveal its true nature. It is even possible to completely hide the app in the launcher, until a system event like a phone call to a specific number or a certain wifi network is connected, to make the app reveal itself again.
You can learn how to dynamically switch your app’s icon on the Chainfire blog and see the code in action on the CameraV repo here. To block screenshots of your app, you can set the FLAG_SECURE feature in any Activity. To complete stop your app from showing up in the recent app list, just set ‘android:excludeFromRecents=“true“‘ in the Activity entry in the manifest.
These are just some of the initial ideas and techniques we have gathered and implemented. We plan to provide this set of capabilities in all of the apps we offer, and hope to spread them as standard features that any app that contains sensitive data or is meant for use by people in high-risk situations, should offer. I would love to hear your thoughts on other techniques that could be used, see code snippets you might have to achieve those, or discuss how and when this whole concept may or may not be effective.
For now, stay safe out there, and that goes for your data and apps, too!
_“Tanzania 0607 cropped Nevit” by Nevit Dilmen (talk) – Own work. Licensed under CC BY-SA 3.0 via Wikimedia Commons_