It is no secret that we are big fans of open-source here at Guardian. In fact, it is what we are made of. Guardian is not just a single app or just one phone, it is a vision for a more private and secure future for personal mobile telecommunications. As part of our work, we are constantly on the lookout other similar, like-minded projects that are developing open-source communications tools for the Android OS which we can make to work with our underlying security platform.
BEEM – Android XMPP happens to be one of these. You can find BEEM in the Android Market or you can download it here. The goal of BEEM is to provide a full featured and easy to use Jabber client on Android. Jabber is another name for XMPP, the Extensible Messaging and Presence Protocol, which is another name for Instant Messaging and Status Updates. XMPP is the open-protocol that grew out of the AIM vs. Yahoo vs. MSN vs. ICQ protocol wars of a few years ago. It is now managed by a standards foundation, and is supported by an amazing number of client and server apps.
Beem, available as source code and in the Android Market, is a great looking, highly functional IM application that supports a number of advanced options including SSL/TLS support and SOCKS Proxying. These two features make it ideal for use with running over the Tor anonymity network and Orbot. By combining Beem with Orbot, mobile instant messaging can be more private (even anonymous if one chooses), usable without fear of eavesdropping by network operators, and made accessible in places where filtering technologies blocks access to popular instant messaging services.
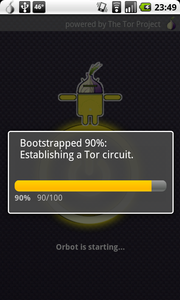
1) Connect to the Tor network using the Orbot app
First, if you do not have Orbot installed, first download it from the Tor Project or scan the barcode below:

The Orbot app contains an HTTP and SOCKS proxy server which allows any Android app to proxy its network traffic through Tor. By installing and activating Orbot (tap on the big power button!), this proxy server is activated and runs in the background as long as you are connected to the Tor network.
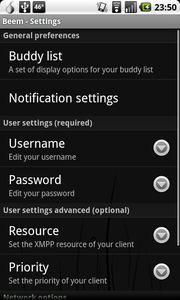
2) Configure your XMPP-compatible account using Beem settings
If you don’t have BEEM installed, you can download it here or scan the barcode below:

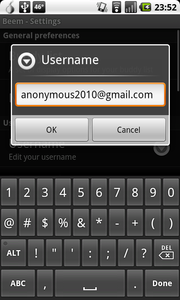
You can use any XMPP service, but we recommend one that supports TLS or SSL security. You can use your Gmail / Google Talk account or you can find a list of public services here: http://xmpp.org/services/
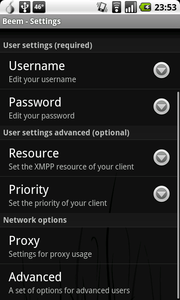
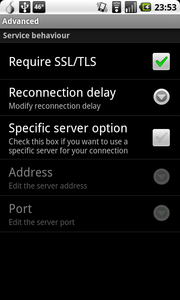
3) Check the SSL/TLS option in the Advanced Menu
You must enable this option to protect your password and chat communications when they exit the Tor network. You can learn more about exit node eavesdropping on the TorFAQ.
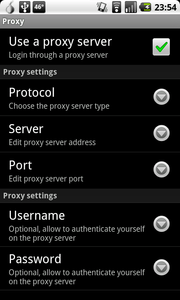
4) Enable the SOCKS Proxy Setting in the Proxy Menu
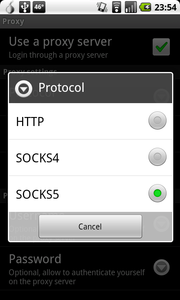
The “Use a proxy server” should be checked, the Protocol set to “SOCKS5”. The Server is “localhost” and the Port is “9050”. You must use the SOCKS5 protocol, as it ensures that domain name resolution is also routed through Tor, stopping from someone snooping on which chat service you are using.
[](https://guardianproject.info/wp-content/uploads/2010/05/socks5.png)[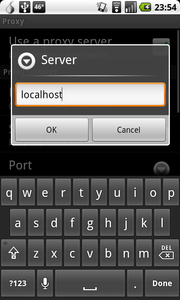 ](https://guardianproject.info/wp-content/uploads/2010/05/localhost.png)[
](https://guardianproject.info/wp-content/uploads/2010/05/localhost.png)[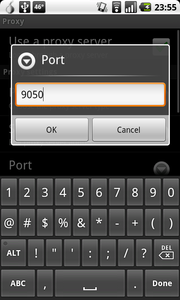 ](https://guardianproject.info/wp-content/uploads/2010/05/port.png)
](https://guardianproject.info/wp-content/uploads/2010/05/port.png)
5) Connect to the XMPP Service
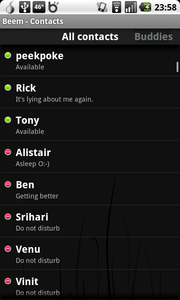
If Orbot is connected, and you have configured the proxy settings correctly, you should be able to connect and see your contacts or buddy list. From here, you can use Beem as you normally would (download user documentation here).
IMPORTANT: To ensure Beem is routing through Tor, you should deactivate Orbot, and then try connecting to your XMPP service with Beem again. This SHOULD fail, else you haven’t setup the proxying correctly.
6) Chat away!
At this point, you should be happily chatting away with your buddies. It is important to note that this solution DOES NOT provide end-to-end encryption, so once your chat reaches the server, it is not secure, both because the service provide can view it if they choose, and the other members of your chat may not be secured themselves.
We do plan to implement and end-to-end extension to Beem using the Pidgin+Off The Record approach that has provided effective on desktop systems. If anyone wishes to contribute development cycles to this effort, please let us know!
If you find issues with Beem, please report them: http://www.beem-project.com/projects/beem/issues/new
If you find issues with Orbot, please report them: https://trac.torproject.org/projects/tor/newticket