We have been experimenting with the Yubikey, a USB hardware password token, a bit over the last few weeks and would like to share our initial findings. We have not received any financial support or donation from Yubico for this work. We simply think they have a very affordable, interesting product that, due to its design, does *not* require any on-device driver software and can easily work with any Android device that supports USB Host/HID mode.

Yubikey is small, light and attaches to a keychain
Our motivation for investigating this device was in finding a way to encourage the use of strong (aka long, mixed-case, etc) passwords on mobile devices, for use with SQLCipher, screenlock passwords, and on boot disk encryption. The issue is that most users rely on short PINs or a visual unlock pattern, which does not provide enough randomness to ensure security of their data. In addition, due to the use of a touchscreen, fingerprint oil smudges on the screen often reveal the numbers entered or the pattern drawn to unlock the device (See the “Smudge Attacks on Smartphone Touch Screens” paper.)

On-screen password entry can leave smudges (Gizmodo)
Even when a user enters a traditional character based pattern, it is often laborious on a mobile device to use symbols and mixed case characters.

Yubikey with inexpensive micro-USB adapter
The Yubikey is a hardware token that plugs into a USB port, and is activated by a short press on the touch sensitive gold-colored disc. It essentially looks and acts like an external hardware keyboard, which is how it works in a drivelress manner. While the primary function of the Yubikey is as a generator for one-time passwords to be verified over a network with a back-end authentication system, it can also be used to store and generate local strong static passwords. It is the static password mode which we have initially worked with for use with Android devices, in order to do local authentication for disk encryption, screen unlock and local encrypted application databases. (We do plan to investigate the other modes of the Yubikey in future posts.)
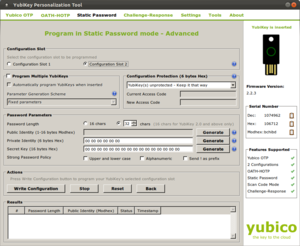
Yubikey Personalization Tool – simple and free
Android has a limit of 17 characters for its disk encryption and screen unlock password. Using the Yubikey Personalization Tool, we were able to generate a strong password of that limit, as well as a 13 character password, which we combined with a memorized, manually entered 4 digit pin. By combining the long password from the Yubikey with a short memorized version, a certain amount of security is preserved even if the key is physically stolen along with your mobile device.

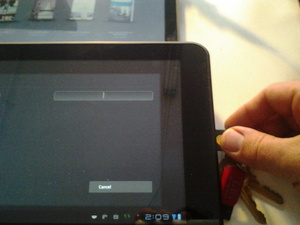
Yubikey activation via micro-USB on Motorola Xoom
__At this point in time, it seems that only Android tablets, such as the Viewsonic GTab, Motorola Xoom and Toshiba Thrive support the necessary USB Human Interface Device mode to enable the Yubikey to work. We have not yet found a smartphone that supports external keyboard hardware, but we are sure they are out there, or else it will not be long. Our initial tests were with the Motorola Xoom, which only includes a micro USB port. Fortunately, using a very simple adapter purchased on Amazon, we were able to make it work. Open the Android settings to the Location & Security screen, and configure your lock screen to be “Secured with password”. When asked to type it in, plug in the Yubikey with adapter, touch the disc, and the pre-configured static password spits out into the password field that is currently in focus on the device.
The Toshiba and Viewsonic tablets offer full-size USB ports, which makes the use of the Yubikey much easier, as seen below. However, as a best practices policy, even if the key can be left plugged in to the device while in use and in motion, it makes most sense to remove the Yubikey immediately, and have it attached to a keychain or other physical item you always keep on your person.
Yubikey also offers an RFID-enabled version of their key which is compatible with the Near Field Communication (NFC) technology found in some newer Android phones. Using this solution, it may be possible to not require actually plugging in the key at all, but instead just having it in the vicinity of your mobile device. You would still need to combine this with a short directly entered password or PIN, in case the NFC signal is somehow wirelessly sniffed by an attacker, though the risk of that is very low for most typical deployments, and NFC itself does provide some amount of security.
All in all, we find the Yubikey to server a useful purpose in improving the base level of local device security on compatible Android devices. While one could type in a 17 character, mixed-case, number and symbol password directly into a device, it would grow old quickly, especially with typical, end-users. The act of plugging in a Yubikey takes very little effort, and combined with a short manually entered PIN, provides the maximum amount of password security for disk encryption, screen locking, and application-based security on Android.
Look for future posts on the use of the Yubikey and other hardware token devices, specifically investigating their use in one-time password, challenge-response, and RFID/NFC modes.